Securing protected patient information (PHI) is no small feat for practices to achieve.
As an aesthetics business, you already know that patients will share all sorts of information with you — from treatment plans and photos to medical history and consent forms. And you also know that you must protect and secure this sensitive information to prevent breach risks and achieve efficient HIPAA security.
Without having this security blanket, any PHI you manage can easily become subject to data exposure. If this happens, it can damage your patient’s trust, put you in violation of HIPAA compliance, and potentially lead to severe violation penalties for your practice.
Being HIPAA compliant means protecting all patient information (PHI) your practice and its business associates manage, including physical ones. But, what happens when you have to protect sensitive information that patients share electronically?
🥁That’s what the HIPAA security rule was created for —
If your first thought was ‘the what??’ — you are not alone. HIPAA compliance can be a doozy, and its different rules, some on privacy, others on breach reporting, can easily confuse you.
But understanding the security aspect of managing electronic patient data is critical for successfully avoiding security risks, violations or fines, as well as patient complaints.
Let’s ease you right into it…👉 In our blog, we delve into how the HIPAA security rule works, which security standards you need to uphold, and how your practice can meet its requirements without any consequences.
HIPAA security rule, in a nutshell
The security rule was first introduced to HIPAA in February 2003. However, it was further updated and took full effect only in 2005, as healthcare organizations began handling more protected patient information (PHI) electronically.
Compared to HIPAA’s privacy rule — which details how your practice should protect physical PHI — the HIPAA security rule details how you should protect any PHI you share or store electronically. This is known as electronic protected health information, or ePHI.
In essence, the HIPAA security rule ensures that —
- Every covered entity — such as healthcare organizations like your practice, health plans, and health clearinghouses — has implemented three main safeguards — administrative, technical, and physical.
- Every business associate (BA) with access to your practice’s ePHI also implements these same safeguards — and to the same extent as you.
When implemented accordingly, HIPAA’s security rule safeguards will protect the integrity, confidentiality, and availability of your ePHI. All electronic patient information, like treatment plans and prescriptions, will stay protected for as long as you monitor and update your security compliance efforts.
HIPAA compliance just got easier— download our FREE HIPAA compliance checklist to ensure you cover all steps successfully! 👇
What security measures do you need to implement?
The HIPAA security rule proposes certain security measures for practices to take, like risk analysis and encryptions. But, HIPAA leaves it to health organizations to decide what security measures they need to stay HIPAA compliant, whether it is access control, ePHI encryption, or else.
This means you get to choose what security measure works best for your practice, which then gives you all the more compliance flexibility. For example, if you are a beauty clinic that uses more devices for storing ePHI like patient before-after photos, you might need to focus on securing your devices better. If you are using additional software, you might need to use their encryptions or security tools.
Although, if you find it harder to choose which security measures to take, you can always go by HIPAA’s three official security standards.
Before you put security measures into place, you first need to consider:
- The size of your organization
- The complexity and volume of your ePHI
- Your tech tools, devices, and software that contain ePHI
- Any existing ePHI risks, and their potential impact on your ePHI
- How you will implement those measures to ensure ePHI security
- The cost of the security measures you’ll implement
Keep in mind that the bigger your medical spa or beauty practice is, the more ePHI you will handle. And the more ePHI you handle, the more security measures, like audit logs software, you will need to implement to protect ePHI from threats.
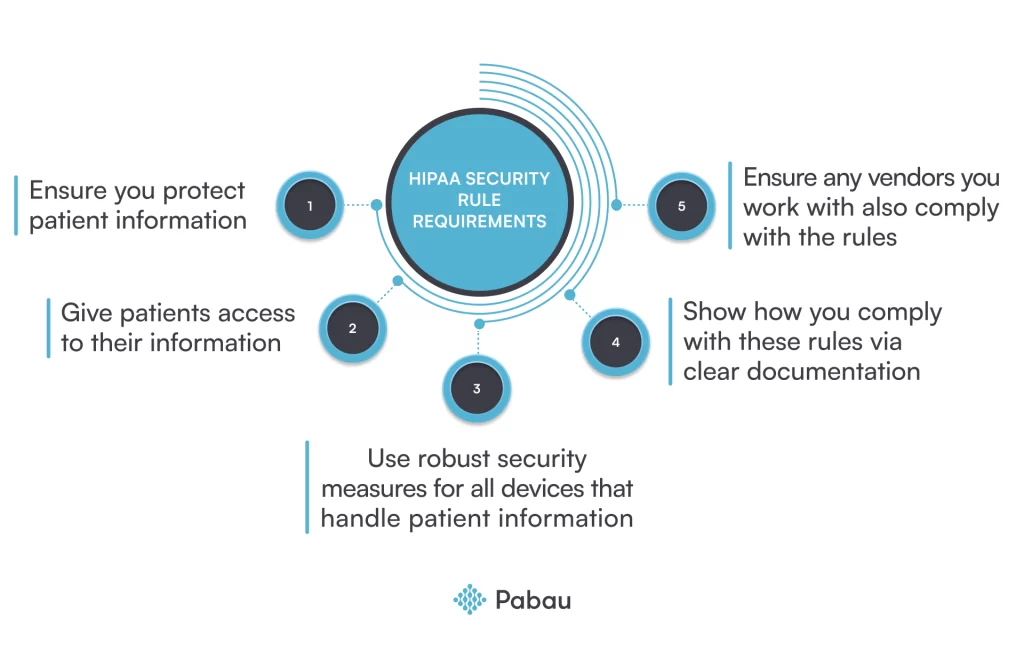
Key requirements of the HIPAA security rule
The HIPAA security rule requires that any security measures you implement, can:
- Protect all digital patient information (ePHI) you share, store, or manage
- Give patients access to their ePHI when they request it
- Monitor and manage all devices that contain ePHI, like iPads and laptops
- Document how you have complied with the rule, e.g. risk analysis proof
- Ensure your BAs also comply with this rule, e.g. software that stores your ePHI
This rule also obliges your practice to continuously monitor the success of all applied security measures. Monitoring is not a ‘set it and forget it’ — you need to do it regularly to ensure compliance to resolve or avoid security compliance violations, and potential fines.
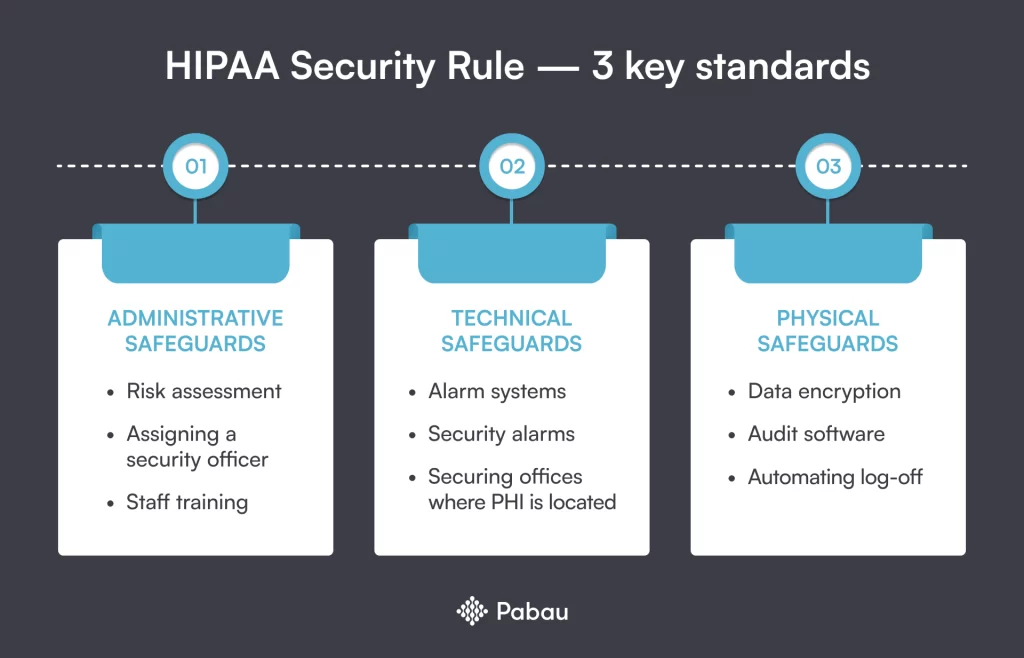
Three key standards of HIPAA Security Rule
The HIPAA Security Rule has outlined three standards that both your practice and your business associates need to comply with. These standards apply to implementing specific administrative, physical, and technical safeguards that HIPAA considers pivotal.
Let’s see how you can comply with each of these standards successfully.
1. Administrative safeguards
Administrative safeguards help your med spa or healthcare practice effectively manage and protect electronic protected health information or ePHI.
In practice, complying with HIPAA’s administrative safeguards means:
- Performing regular risk analysis and risk management to secure your ePHI
- Creating detailed documentation on which security measures you implemented, how you implemented them, and how those measures helped you secure ePHI
- Maintaining the security of your ePHI and adopting new measures when needed
Out of 146 healthcare facilities, only 33.5% have completed their required risk analysis. This means that 33.5% of healthcare businesses now have higher risks of having their ePHI breached when they could have done more to protect it.
Your practice’s top goal is to protect ePHI from threats. So, the last thing you want to stop doing is regular risk assessments. Flaking on quality risk analysis and management loses you money, status, and patient trust. Plus, it puts you in potential conflict with the law and makes you subject to violations and penalties.
Here’s how you can easily comply with HIPAA’s administrative safeguards —
- Conduct ongoing risk assessments to detect potential ePHI breaches
- Introduce a risk management policy and share it with BAs and colleagues
- Create an emergency response plan and test it; then test it now and again
- Provide employee training on cybersecurity and HIPAA compliance
- Restrict access to ePHI for third parties — like non-medical staff, family members, providers uninvolved in the patient’s care, and others who don’t need ePHI access.
- Appoint a security officer to safeguard ePHI, manage the potential risks, and oversee your overall compliance efforts.
Report incidents affecting over 500 people to the Office for Civil Rights (OCR). It is your legal obligation, so you don’t want the OCR to beat you to it.
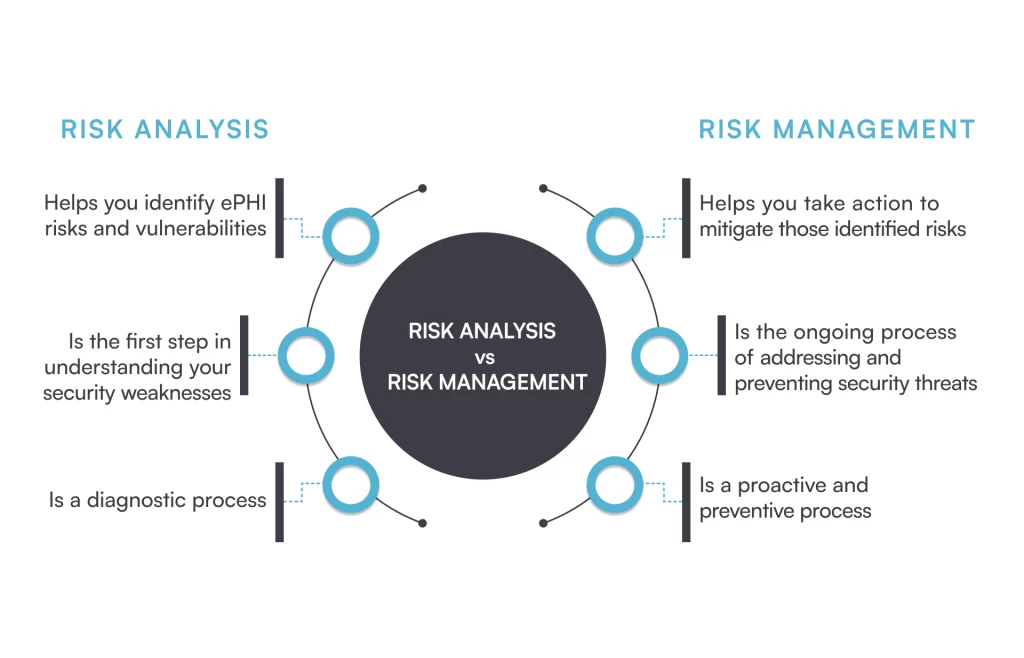
Finally, understand the difference between HIPAA risk analysis and risk management.
2. Physical safeguards
The HIPAA security rule does not protect physical PHI, like those you keep on paper — that is the aim of HIPAA’s privacy rule. But, the security rule does protect any electronic patient information (ePHI) that is physically stored within your practice, such as:
- Alarms or security systems that protect servers, data centers, or areas where ePHI is stored, like labs.
- Workstations or devices that contain ePHI, like patient photos stored in an iPad
- Areas where ePHI is stored, like record keeping or treatment rooms.
Whether it’s accidental or intentional, 61% of data breaches happen due to employee negligence. This means that anything — from improper handling of medical data in the workplace to leaving your devices unattended — can lead to disclosure of ePHI.
Here’s how you can easily comply with HIPAA’s physical safeguards
- Limit physical access to any facilities that contain ePHI by using access controls like smart locks, and authorized access cards.
- Give authorized access to these facilities only to those who need it, like the patient’s healthcare practitioner.
- Control access to devices that may contain ePHI, like laptops and phones. Create policies to specify how these devices will be used and by whom, and inform your team.
- Create strong password policies for all devices that contain ePHI
- Set workstations to log off or switch to screensavers in 15 minutes or less.
- Create policies on how you’ll transfer, remove, and dispose of ePHI
3. Technical safeguards
The HIPAA security rule also requires you to follow specific technical safeguards to shield ePHI. These safeguards include using firewalls and encryption, securing your hardware and software, and implementing data backups. Basically, any technical process that secures ePHI belongs here.
In essence, you will need to follow these technical safeguards:
- Create technical policies and procedures to control who has access to ePHI
- Perform audits by implementing hardware tools and using audit software.
- Examine who has access to the systems that contain or use ePHI, and limit access to only those who need it, like patients themselves.
- Create policies and procedures to clearly state that your ePHI has not been, nor it will be, incorrectly edited or destroyed.
- Introduce measures to protect unauthorized access to ePHI in an electronic network, like digital signatures.
Here’s how you can easily comply with HIPAA’s technical safeguards
- Check who has access to your ePHI and if they need that access at all. Restrict or limit access for medical and non-medical staff who don’t need to have it.
- Give patient access to their ePHI — it is their legal right to access, edit, or update their data.
- Perform regular audits to ensure there have not been any ePHI threats. Or cut your work in half and use a medi-aesthetics audit software to keep activity logs and see changes in patient data when they’re made.
- Securely destroy ePHI, via data wiping or e-waste disposal services.
- Encrypt your ePHI even further. What your medical software needs is to automatically encrypt ePHI for your practice, and save you the headache.
- Implement automatic sign-outs and session timeouts to log you off all devices. With a 2FA authentication in place, your ePHI will be more shielded against risks.
Whenever you’re dealing with protected health information, you must always inform patients of what they can and can’t do with their data. You also need to let them know how their PHI is secured and handled.
As with the other two safeguards, you need to monitor your security measures, too. Make updates where needed and know that HIPAA compliance is prone to changes, meaning you and your BAs must keep track of the latest news.
What if you violate the HIPAA security rule
Are there any loopholes in the ePHI security measures you implemented?
Is there something more you could have done to shield your ePHI?
HIPAA violations are real and legally binding — so you need to take them seriously. Under HIPAA, it is your practice’s obligation to protect all patient health or personal information that you, and your business associates, handle electronically.
Violating the security rule might happen intentionally or unintentionally. But whether it was your fault or not, violations can result in a HIPAA investigation, heavy fines, and even jail time — if the violation is criminal.
Depending on the violation nature, here are the HIPAA fines you might be looking at:

The best way to detect security rule violations early on is to do regular risk analysis, compliance training, and security policy updates. By pinpointing security risks early on, you can act faster to resolve them — and save yourself the penalty or investigation.
HIPAA security rule violations — cases to learn from
1. L.A. Care Health Plan
L.A. Care Health Plan is a local agency providing health coverage in Los Angeles. They violated the HIPAA Security Rule due to inadequate risk analysis, security measures, and record reviews, which ended up disclosing the ePHI of 1,498 individuals. Following a filed violation complaint, the OCR performed two investigations and settled the case for $1,300,000.
2. David Mente, MA, LPC
David Mente is a counselor and therapist in Pittsburgh, PA. When he violated the HIPAA Right of Access, by not providing a father with his minor children’s health records, the OCR provided him with technical assistance to solve the issue. When the OCR checked that their technical recommendations were not implemented correctly, the practice was fined, and the case was settled for $15,000.
3. Life Hope Labs, LLC
Life Hope Labs, LLC, in Sandy Springs, Georgia, violated the HIPAA Right of Access when they didn’t provide an individual with the medical records of their deceased father 225 days after the initial request. As a result, the OCR investigated the case and the diagnostic laboratory was fined $16,500.
An expert’s take on HIPAA security rule

Joseph Harisson
IT expert at IT Companies
👉 Joseph Harisson is a seasoned IT expert at IT Companies with a diverse background in system administration, network support, cybersecurity, and cloud technologies. As a member of both the National Society of IT Service Providers and the Information Systems Security Association, he shares how the HIPAA security rule can apply to medi-aesthetics and beauty businesses in the US.
“Aesthetics, beauty, and medi-spa/salon businesses may collect and
store a variety of PHI, such as customer contact information, medical
history, and treatment records. It is important to implement and maintain
security measures to protect this PHI from unauthorized access, use, or disclosure.
These businesses may also use a variety of cloud-based services to manage their operations. It’s important to choose cloud-based services that offer strong security features and to implement appropriate security controls to protect PHI stored in the cloud.”
He also shares practical tips for medi-aesthetics practices to follow when complying with the HIPAA security rule —
✨ Use strong passwords and multi-factor authentication.
✨ Keep your software up to date.
✨ Be careful about what information you share online.
✨ Be aware of phishing scams and other social engineering attacks.
✨ Have a plan for responding to security incidents.
Unlock efficient HIPAA compliance with Pabau!
The consequences of not complying with the HIPAA security rule can affect your practice financially and legally, waste your time, and impair the trust you build with patients.
One solution to mitigate security challenges faster is to apply security software solutions. An all-in-one practice management software, like Pabau, can ensure your ePHI won’t go unsecured —
- Automated audit logs? Check!
- Extensive data encryptions & secure ePHI storage? Check!
- 24-hour sign-out sessions & timeout sessions? Check!
Pabau helps support your HIPAA compliance automatically, saving you time, effort, and compliance worries. Explore our blog to learn more or download our FREE HIPAA compliance checklist to get started! 👇





